My Twitter Got Hacked, What Next? The Obvious, Less Obvious & Forensic
And there goes the morning. If I could describe a deeply annoying start to the day, it would be thus:
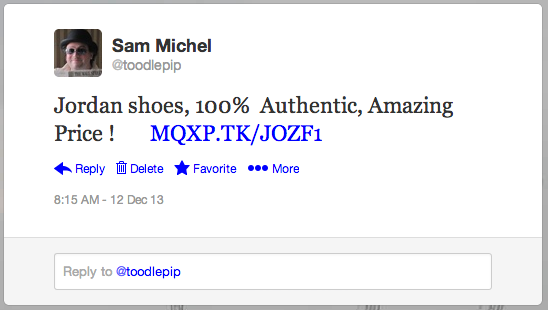
Wake up to discover that you’re offering your Twitter followers a sweet deal on Jordan’s (whatever the hell they/s/he is/are). Then follows a flood of tweets, direct messages, emails, text messages and the other half shouting across the room, “your Twitter account has been hacked”.
In a word: Balls (there were children present)
Help from Twitter
There’s some useful pages on Twitter itself to deal with compromised Twitter accounts (sounds better than hacked doesn’t it?). If a bad guy/gal has changed your password and you can’t access the account, there’s a contact form specifically for this.
The Bleeding Obvious
Change your password. I’ll say it again, change your password. No, not to the one you use for everything.
The problem with using the same password is that you’re only as safe as the weakest site you’ve used it on. That daft Facebook game? The dodgy dating site? Yup, that could be the weakest link, but so could your registration on a larger site.
In a seemingly endless round of stolen password stories, the latest victim was Adobe, where millions of users’ details were swiped. The data is in the public domain and you can check whether your info was listed using this Adobe Account Hacked check tool.
How can you remember all those passwords? Fair point. Fortunately, there’s some useful apps like Lastpass help create and manage secure passwords and work across laptops, smartphones and tablets. (disclosure: happy customer here). You can still have your one password but that only unlocks the super-strong passwords that you’ll use everywhere else.
Don’t forget to dive in to your account and make sure you delete the offending tweets (tip: the trash icon on your timeline will let you zap ’em)
The Less Obvious
To be extra safe, you can get Twitter to send you a text message with a PIN code on each login. The PIN code must be entered before you can access the account. It’s pretty easy to setup and means a baddie needs both password and mobile phone (unlikely) to access your account.
Setup is dead easy: register your mobile number with your Twitter account, then, turn on Send login verification requests. Voila! You can also use the Twitter app on your smartphone to verify logins.
Whilst you’re at it, Google has the same function on it’s logins, called 2-step verification. Worth a moment?
Remember all those other sites and apps where Twitter is used to login? Given that it’s time to tighten security, reviewing which sites have access is probably a good thing. Once they have access, they keep it, even if the password changes.
Review which applications have access to your account using the Apps option on your account. Anything you don’t recognise hit that Revoke access button. Be cautious, it only takes 2 secs to re-authorise an account. Better safe, than sorry. I hadn’t checked this in a while and had over 60 apps authorised to tinker with Twitter on my behalf.
Forensics
OK, so what the hell happened? Chances are it was simply a hacker using a list of emails and passwords to gain access. But just to be sure it’s worth checking how the offending tweets were posted.
Twitter stores a field called ‘source’ for every tweet published. It’s not show in their own apps or website, but Hootsuite does show this information (hat/tip @spiderworking).
Why’s this useful? Well, if the source is something like Web, or Mobile Web then the tweet is likely to have been from a compromised password. If something different is listed, it may be an application that has gone rogue or been hacked itself (remember Revoke access above).
Unfortunately, there doesn’t seem to be a way to track down the IP address of the spammer through Twitter’s publicly available data (for good privacy reasons) – but it would be useful in tracking down the culprit (Twitter, are you listening?).
You’re Not Alone
If it’s happened to you, welcome to the club. Empathise, gather for a group hug. You are not alone. And it’s not just us peons, the big shiny corporates like Burger King, The Guardian, HMV and Paypal have all fallen prey.
Thanks to everyone who contacted me about my account, especially @gringomoses @mediaczar @spiderworking.





